HARD DISK DEGAUSSING SERVICE
Certified On-site Data Destruction and Erasure Solution
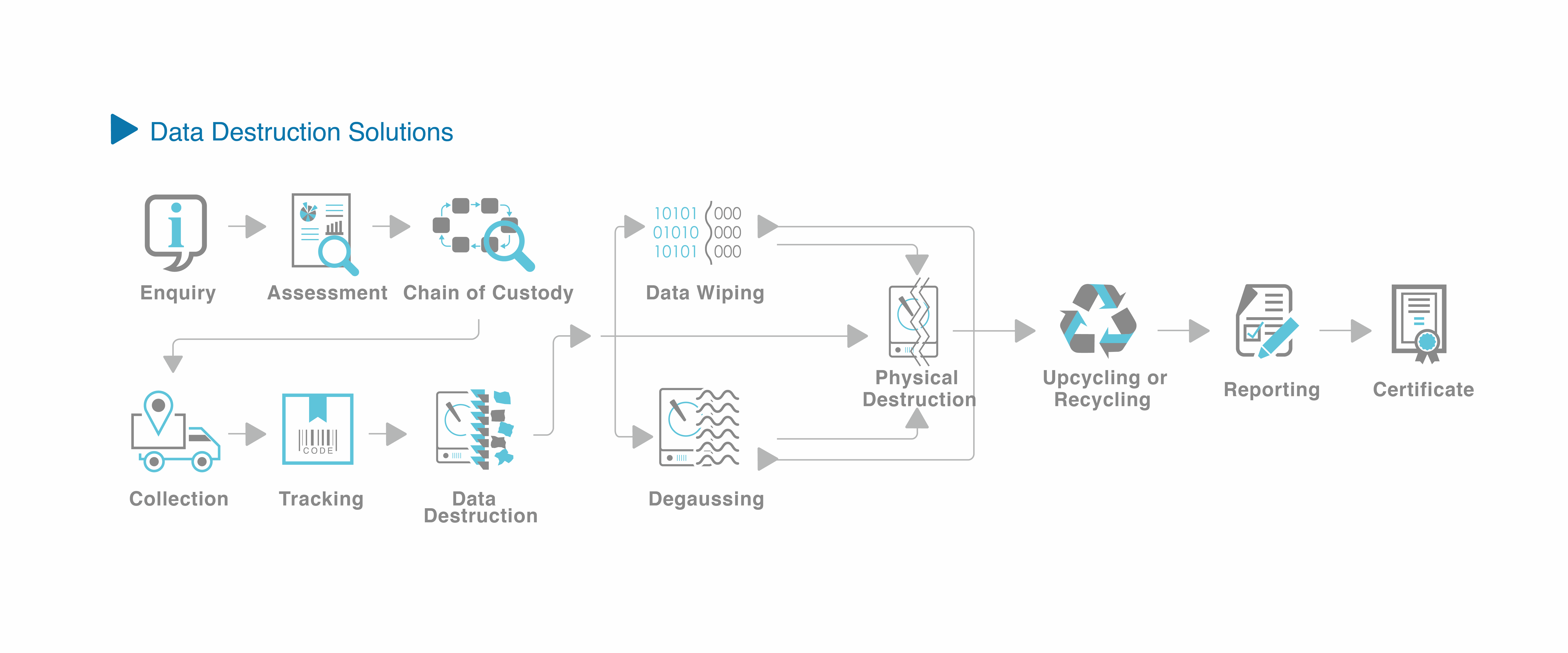
Secure data destruction is the first priority for corporations to dispose of old IT equipment, used to prevent the risk of data breaches, which would damage a corporation’s reputation and induce a huge loss. Instead, a proper data destruction strategy can facilitate redeployment or donation to fulfill sustainable development goals.
EcoSage is a hard disk degaussing company in Hong Kong and the APAC region with hard drive wiping service, we provide ISO 27001 certified one-stop solution that manages all aspects of secure and sustainable data destruction including GPS tracked collection, inventory validation, on-site hard drive degaussing, SSD data wiping, and crushing. Regardless of which solution or combination of solutions you select, you will receive a Certificate of Data Erasure & Destruction with supporting reports to ensure chain of custody.
Looking for a certified and reliable Data Destruction partner?
Compliance
EcoSage is accredited to the highest standards as a security data destruction provider in Hong Kong and other countries in the Asia Pacific region. Our license certifications and awards give confidence we are a trusted and responsible shredding company. We meet the highest standards available for our data destruction services.
See our standards, certifications and accreditation detailed here






On-Site & Off-Site Data Destruction
Depending on your needs, EcoSage provides solutions for on-site and off-site data destruction. By choosing EcoSage, you’re partnering with a security and environmental company that follows data destruction and eco-friendly best practices. No matter on-site or off-site, we handle all documents with a consistent chain of custody, resulting in a tightly controlled and well-documented destruction process.
On-site Data Destruction
“Destroy at your premises and convenience under your with”
Secure onsite data destruction is an ideal solution for customers requiring the immediate or witnessed destruction of confidential, copyrighted or royalty-based materials directly on-premises.
Off-site Data Destruction
“Cost-effective destruction service for bulk quantity”
Secure, convenient, environmentally friendly and cost-effective, secure offsite data destruction is an ideal solution for customers that need ongoing, verified destruction of sensitive and confidential data bearing media at our state-of-the-art, high capacity and controlled processing centre.
Destruction Option: Data Wiping, Degaussing, Crushing
What are the options for secure data erasure?

Hard Disk Degaussing Service
EcoSage offers high power on/off-site military grade and US NSA approved hard disk degaussing service hk for magnetic devices. Magnetic hard drives, tapes, storage devices and storage media are rendered completely inoperable after the degaussing process.
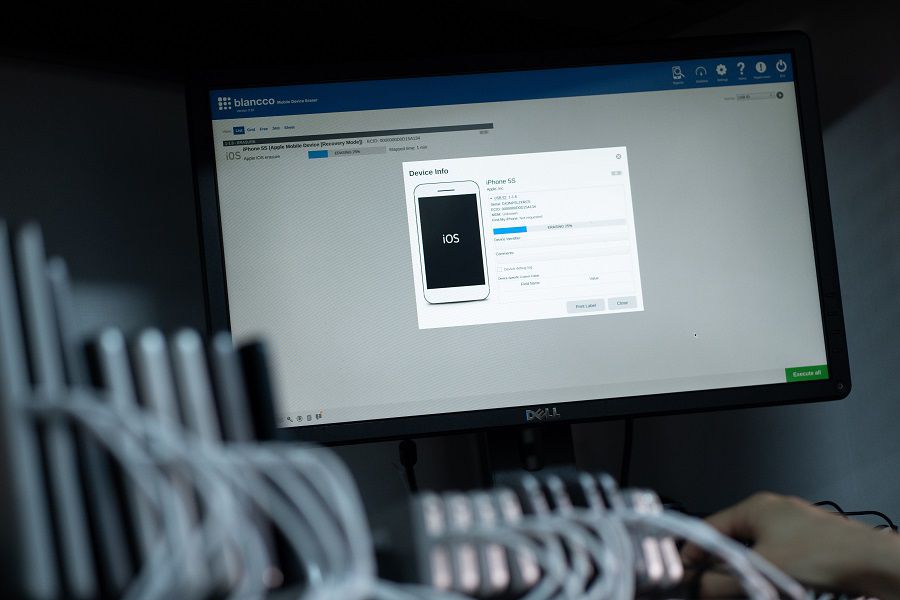
Hard Drive Data Wiping Service
EcoSage provides on/off-site data wiping (such as hard drive) service by certified data erasure software Blancco. Every data erasure performed produces a Certificate of Erasure. It also ensures that the maximum residual value can then be sought for the resulting redundant IT assets.

Physical Destruction
The storage media can also be destroyed physically by methods such as shredding and compacting. It is recommended to physically destroy the items after degaussing or data wiping. After physical destruction, the storage media can no longer be reused again.
Type of Media
Not only computers and servers store digital data, portable media, such as mobile phones, tokens, USB thumb drives, CDs and DVDs, as well as copiers, printers and network devices can contain data and sensitive configuration, when overlooked and left intact, may compromise the company, client and employee privacy.

Backup Tapes
Tapes such as LTO, DDS, DLT can be either on-site or off-site degaussed, depending on client requirements, tapes can be shredded at our processing centre.

Magnetic Hard Drives
EcoSage offers on-site and off-site erasure, crushing, degaussing and shredding solutions.
Solid State Drives
Data erasure allows for reuse of the drives, while shredding of solid state drives offers a proven solution when clients do not want solid state drives reused or resold.

Storage and Network Equipment
Hard drives of storage array or SAN storage on this equipment need to be destroyed by either degaussing or physical destruction. Like other data-bearing devices, most network equipment store network IP address or other network configurations which make loopholes in IT security.

Optical Discs
The most common destruction option for CD / DVD / Blu-ray Disks belongs to the physical destruction by shredding where the materials are recycled after their destruction.

Mobile Devices
Shredding provides organizations with an additional measure of confidence that the information stored on these items is safely destroyed. The memory from mobile devices can be erased for remarketing or destroyed through shredding if reuse is not desired.

Office Equipment
Advanced office equipment, including printers, copiers, and scanners can be the source of unexpected digital data breaches. Very often these items are equipped with embedded hard drives and nonvolatile memory chips that retain data until that data is destroyed.
Chain of custody
Chain of Custody controls ensure all products are securely managed and tracked through each step of the destruction process. As a hard disk degaussing company hk, we have invested in technology and ERP system to ensure that your products are tracked throughout their journey. Our end-to-end tracking system makes use of barcode scanning at every stage as well as GPS-tracked vehicles.
Depending on your needs, this may include the following documents
-
Identification and scanning of all necessary serial numbers for tracking purposes;
-
A recording of the time of disposition, and the method of disposition;
-
Identification of the individuals executing the procedure;
-
A video recording of the process;
-
A signed Certificate of Destruction proving compliance with relevant regulations.
Logistics
To secure your precious data and avoid data breaching, EcoSage uses non-stop direct logistics to minimize the duration of transportation. In addition, our vehicles are always manned to ensure all of your data are safe before proper destruction.
Certificate and Reporting
At the end of the data destruction process, a certificate will be issued to our client as proof of secure data destruction. Clients may also obtain detailed reports from our portal.
Sustainability
By partnering with hard disk degaussing company EcoSage in Hong Kong and the APAC region, you’ll make a greater impact and get total insight into your electronic recycling progress arising from the data destruction tasks.
Our proprietary report gives you detailed metrics by waste type, time period and location and lets you understand your electronic recycling progress at a glance. Ultimately, we can find out how you can make a big difference to achieve sustainability cost-effectively.
Contact us now!
Contact us now to get more informations.